ITAC
- Home
- ITAC
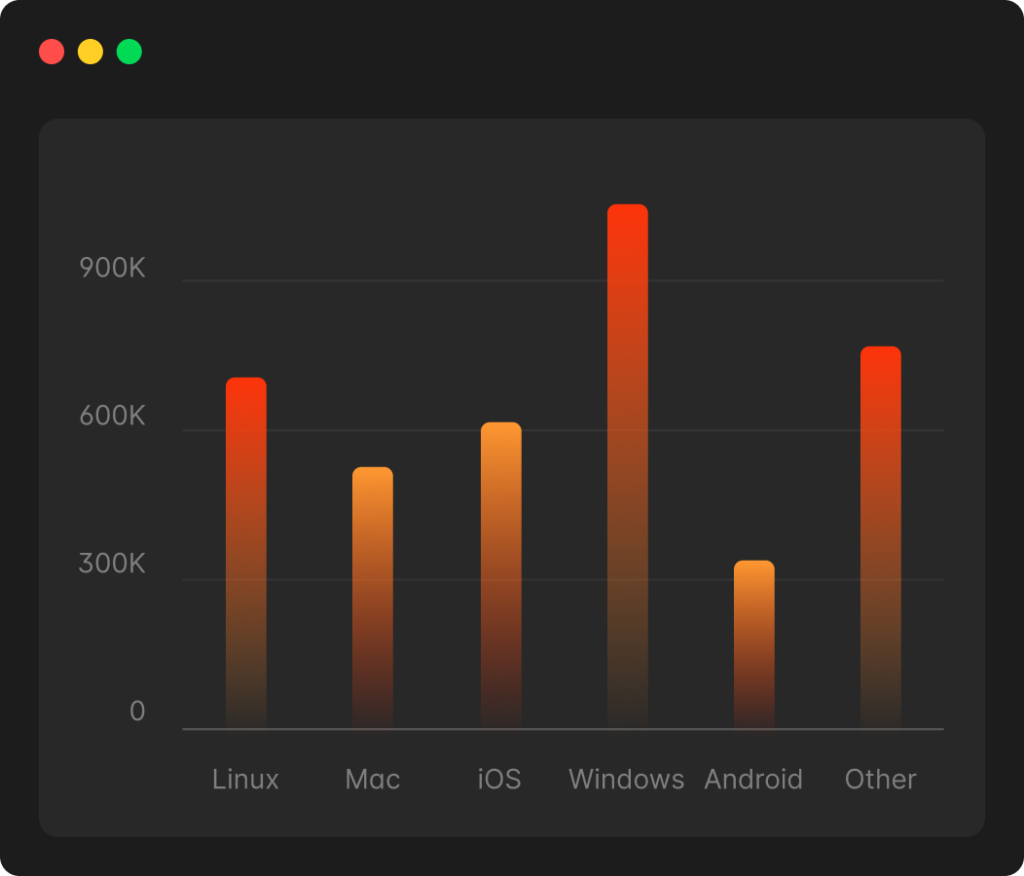
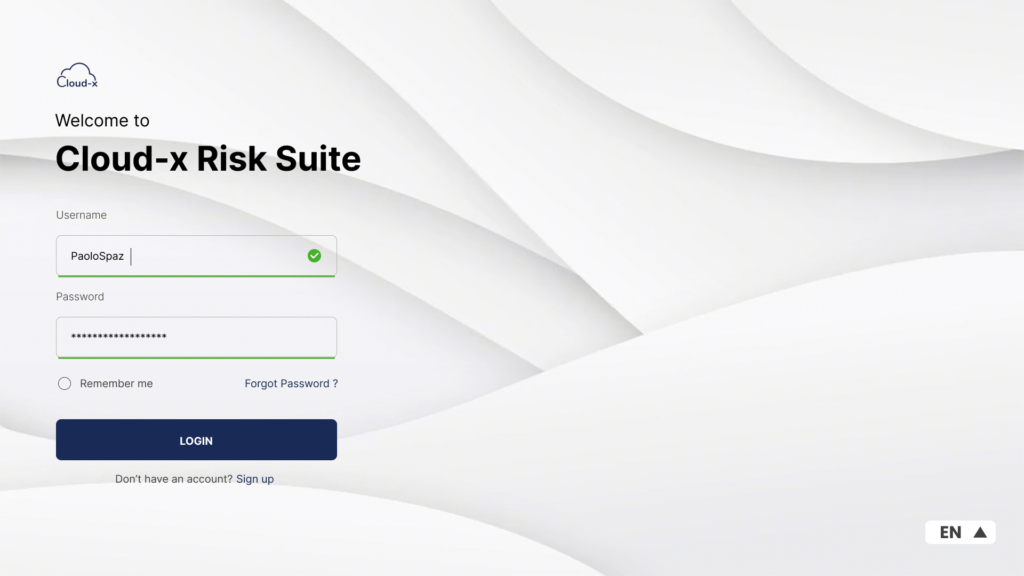
What are IT Application Controls (ITAC)?
Key Components of Our ITAC Solution
Input Controls
Implement validation checks and data integrity controls to ensure that data entered into the application is accurate, complete, and authorized, reducing the risk of data entry errors and fraud.
Processing Controls
Define rules and logic to govern how data is processed within the application, including calculations, transformations, and workflows, ensuring the accuracy and consistency of data processing operations.
Authorization Controls
Manage user access and privileges within the application through role-based access control (RBAC), user authentication mechanisms, and authorization policies, preventing unauthorized access and ensuring data confidentiality and security.
Output Controls
Validate and verify the accuracy and completeness of output generated by the application, including reports, documents, and electronic files, to ensure that users receive reliable and trustworthy information for decision-making and analysis.
Audit Trails
Maintain detailed audit logs of user activities and system events within the application, facilitating accountability, traceability, and forensic analysis in the event of security incidents or compliance audits.
Key Benefits of Our ITAC Solution
Enhanced Data Integrity
By implementing ITAC, organizations can improve the accuracy, completeness, and reliability of data processed and stored within their applications, reducing the risk of data errors and inconsistencies.
Improved Compliance
ITAC helps organizations achieve compliance with regulatory requirements, such as Sarbanes-Oxley (SOX), GDPR, and HIPAA, by ensuring that application controls are designed and implemented to meet specific legal and regulatory mandates.
Increased Operational Efficiency
By automating and standardizing application controls, organizations can streamline data processing workflows, reduce manual effort, and optimize resource allocation, leading to improved productivity and operational efficiency.
Why Choose Our ITAC Solution?
- Expertise and Experience: Our team of ITAC experts has extensive experience in designing, implementing, and managing application controls across various industries and environments, providing you with the guidance and support needed to achieve your ITAC objectives.
- Customizable Solutions: Our ITAC solution is highly customizable to meet the unique needs and requirements of your organization, enabling you to tailor controls and workflows to fit your specific business processes and compliance requirements.
- Scalability and Flexibility: Whether you're a small business or a large enterprise, our ITAC solution scales effortlessly to accommodate your growth and evolving IT infrastructure, ensuring that you can effectively manage application controls across your organization.

